Most of our physical security systems -including our PC anti-theft cables and padlocks- are offered with different, identical or pass key systems. Here are some benchmarks to help you choose the solution that best suits your use.
The different key systems
 Each system comes with its 2 identical keys, and each set is different from the set of another system. All key sets are different, each key opens the lock for which it is intended and does not open the others.
Each system comes with its 2 identical keys, and each set is different from the set of another system. All key sets are different, each key opens the lock for which it is intended and does not open the others.
However, pay attention to the quantities of possible combinations, the number of possible variants for a given lock type may vary from one padlock model to another, depending on its quality or level of security. If you wish to order large quantities (above 500), please consult us.
This system of different keys is good in the event that each user must not have access to the secured property of another user; it also has the benefit of making a user responsible for the property entrusted to him. In this case, we advise the administrator to keep one of the two keys of the set in case of loss.
For most systems, keys are numbered, making tracking easy.
The identical key system
 All keys are the same. 2 keys are provided with each lock, and they are identical. For example, if you order 100 antitheft cables for your computers, they will all have the same lock and key, so you will have 200 completely identical keys in your possession.
All keys are the same. 2 keys are provided with each lock, and they are identical. For example, if you order 100 antitheft cables for your computers, they will all have the same lock and key, so you will have 200 completely identical keys in your possession.
These keys are usually numbered, it is important to use this number to contact us if you have to order the same products again. However, we do keep this information in our secure order archive.
These single key padlock products are not in stock and require special production with a specific key number. This specialised, customized production requires a certain amount of time and extra cost, clearly indicated on all our price grids.
We can deliver several lots (maximum 6 lots, consult us) of identical keys (minimum 10 units per lot) if you wish.
This can be useful in securing different services, sites or buildings independently.
This identical key system is most often used to secure a set of property on the same space, where users do not have access to these keys. This is the typical case for a computer area protection system consisting of desktop computers: users do not need access to the locks, only the administrator and some technicians have access to these keys. To facilitate key management, all locks will have the same key, which acts as a pass. In this case, our customers throw away all except 3 or 4 keys which they keep for administrators and technical staff, as well as a key put in the safe.
The pass key system
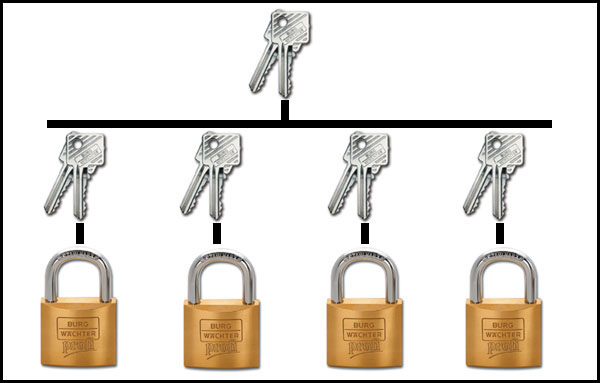 The pass key system is exactly the same as that of the different keys, except that each lock has 2 corresponding keys that only open one lock, not the others, BUT ONLY 1 “pass” key opens all locks. This is the principle that is applied in hotels, where each customer has his own key that only opens his door, but the hotel administration has a general pass key that opens all doors.
The pass key system is exactly the same as that of the different keys, except that each lock has 2 corresponding keys that only open one lock, not the others, BUT ONLY 1 “pass” key opens all locks. This is the principle that is applied in hotels, where each customer has his own key that only opens his door, but the hotel administration has a general pass key that opens all doors.
The pass key is of course the most important and should not be lost. It is usually numbered, it is important to use this number to inform us if you have to order the same products again. However, we do keep this information in our secure order archive.
Only one key is provided free of charge for each order included in this option, but if you so desire we can provide you with several pass keys. Consult us for the price.
These products are not always in stock and require special production with a specific key number attributed to you. This special, customized production requires a certain amount of time and extra cost, clearly indicated on all our price grids.
We can deliver several lots (maximum, 6 lots, consult us) of identical keys (minimum 10 units per lot) if you so wish. This can be useful in securing and separating different services, sites or buildings.
This key system is particularly useful for to making each user responsible for the property entrusted to him or her by his or her company, or when each user must have access only to the property entrusted to him or her, and not to others. The advantage of this solution is for the administrator who can at any time intervene with a single key, which eliminates the cumbersome need to handle a large number of keys. This system is particularly useful for laptops where everyone needs their own key to lock their computer, but where the administrator must be able to unlock if needed.


















